Last updated January 16, 2024
This add-on is operated by Sumo Logic
Log mastery & Metric insights | Real-time analytics & Proactive ops
Sumo Logic is the industry-leading, secure, and purpose-built cloud-based machine data analytics service.
Introduction
The Sumo Logic add-on for Heroku helps you harness the power of machine data with effortless log management that delivers business and operational insights within minutes.
Collect, search, and analyze your Heroku logs using a scalable analytics service. Next, monitor and visualize your data using real-time Dashboards. Finally, create custom alerts to notify you when specific events occur.
Benefits and features
Adapted to your use case
- DevOps: Monitor and troubleshoot your application from code to production. Understand performance, detect critical issues, correlate events, analyze trends, and detect anomalies.
- Applications analytics: Understand how your users use your app, analyze business KPIs in real-time, and optimize your application to deliver the most value to your customers.
- Compliance and security: Ensure that your application complies with regulations such as PCI or HIPAA and that it handles sensitive data securely. Monitor access and other user behavior and detect malicious activity.
Easy setup
Simply select Sumo Logic as an add-on for your application to start viewing and analyzing your Heroku logs in real time.
Collect and centralize
Sumo Logic collects terabytes of data from any app, cloud, device, custom hardware, sensor, server, or network source. Lightweight Collectors replace traditional complex setups and collect, compress, cache, and encrypt the data for secure transfer. Centralized logging eliminates the need for additional archiving, backups, and restores. Data can be pre-parsed and partitioned on ingest. A wide range of Collector and search APIs also help administrators easily develop and integrate data sources with Sumo Logic.
Search and analyze
Run searches and correlate events in real-time using a simple search engine-like syntax, such as PARSE, WHERE, IF, SUMMARIZE, TIMESLICE, GROUP BY, SORT, etc.
Sumo Logic’s patent-pending LogReduce™ technology reduces hundreds of thousands of log events into groups of patterns. By filtering out the noise in your data, LogReduce can help reduce the mean time to identification of issues by 50% or more.
Transaction Analytics automate analysis of transactional context to decrease time associated with compiling and applying intelligence across transactions flowing through your multi-tiered Heroku application.
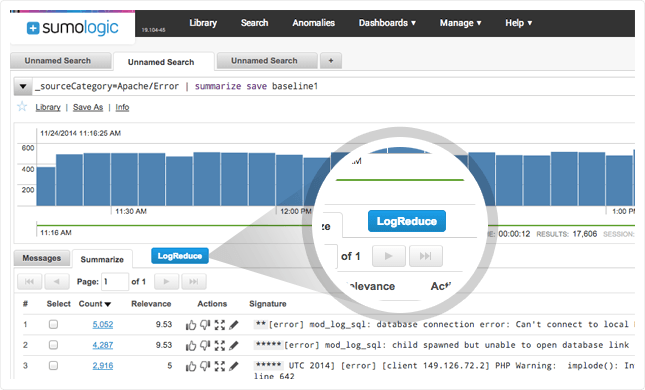
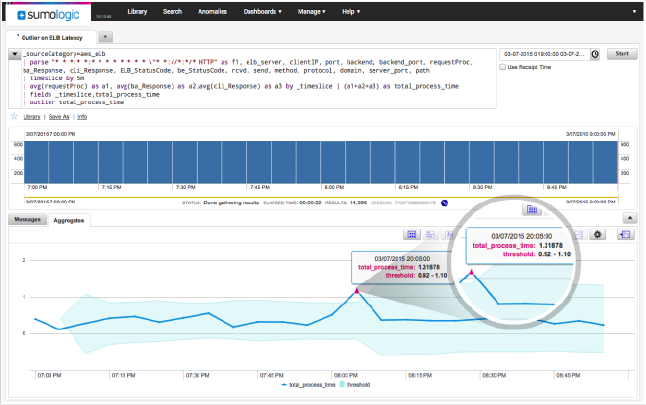
Detect and predict
When rules are not enough, Sumo Logic’s outlier detection, powered by a unique algorithm, analyzes thousands of data streams with a single query, determines baselines and identifies outliers in real-time. Purpose-built visualizations highlight abnormal behaviors, giving operations and security teams visibility into critical KPIs for troubleshooting and remediation.
The predictive analytics capability extends and complements outlier detection by predicting future KPI violations and abnormal behaviors through a linear projection model. The ability to observe violations that may occur in the future helps teams address issues before they impact their business.
Monitor and visualize
Custom dashboards and visualizations help you monitor your data in real-time. The dashboards unify all data streams so you can keep an eye on events that matter. Charting capabilities such as bar, pie, line, map, and combo charts help monitor the most important KPIs for your Heroku application.
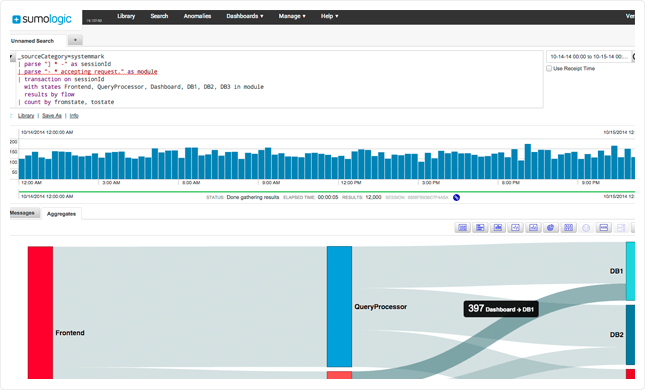
Alert and notify
Custom alerts proactively notify you when specific events and outliers are identified across your data streams. Proactive notifications are generated when your data deviates from calculated baselines or exceeds thresholds to help you address potential issues promptly.
For complete details, go to www.sumologic.com, or see Sumo Logic Help.
Secure by design
Encryption: All data at rest within Sumo Logic is encrypted using strong AES 256-bit encryption and all data in transit is encrypted via SSL.
Secure SaaS: Sumo Logic maintains an array of critical certifications and attestations including PCI DSS 3.0, which also helped develop the robust Sumo Logic application for PCI:
- Compliance with the U.S. – E.U. Safe Harbor framework
- SOC 2, Type II attestation
- Attestation of HIPAA compliance
- PCI DSS 3.0
- FIPS 140 compliance
Provisioning the add-on
Single application
Sumo Logic can be attached to a Heroku application via the CLI:
A list of all available plans can be found here.
$ heroku addons:create sumologic
-----> Adding sumologic to sharp-mountain-4005... done, v18 (free)
Multiple applications
To monitor multiple applications, you can share the same Sumo Logic add-on with multiple applications.
First, provision the add-on for your first application:
$ heroku addons:create sumologic
-----> Creating sumologic-test-horizontal-9854... done, (free)
-----> Adding sumologic-test-horizontal-9854... done
Next, attach the add-on to your additional applications using the name of the add-on returned by the create command:
$ heroku addons:attach sumologic-test-horizontal-9854
-----> Attaching sumologic-test-horizontal-9854... done
You can also provision one add-on for each application using the steps for Single Application, although we do not recommend this method.
Trial account
If you select the Free plan, you will first receive a free 30-day trial subscription.
Your Sumo Logic trial account allows you to try all advanced features to understand how Sumo Logic will fit within your organization. It includes a daily data volume limit of 5 GB per day, with 20 users and 30 days of data retention.
After 30 days, your account will revert to a Sumo Logic free account, with a limited feature set, a daily data volume limit of 500MB per day, with 3 users and 7 days of data retention.
Access
For more information on Sumo Logic features, see the Sumo Logic Help.
Sumo Logic can be accessed via the CLI:
$ heroku addons:open sumologic
Opening sumologic for sharp-mountain-4005
or by visiting the Heroku Dashboard and selecting the application. Select Sumo Logic from the Add-ons menu.
(Optional) Set up field extraction rules for for applications
This step is optional, but recommended, as it makes it easier for you to query your Heroku application logs in Sumo.
When Sumo ingests Heroku application logs, it attaches the _sourceName metadata field to the the data. The _sourceName Sumo assigns varies by application—its value is the unique identifier for the Logplex drain assigned to the application.
For ease of understanding the log data, you can use a field extraction rule (FER) to rename _sourceName from the drain UUID to the application name. For general information about FERs see Create a Field Extraction Rule in Sumo help.
You can determine the drain identifier by running the heroku drains command for your app.
The identifier will look something like:
d.98ee476d-d2d8-46bf-afc2-740f6f7e5b2a
Then, define an FER in Sumo.
In the Sumo web app, go to Manage Data > Settings > Field Extraction Rules.
Click the plus sign (+) in the upper left corner of the page to display the Create Field Extraction Rule popup.
Rule Name. Enter a name for the FER.
Scope. Enter:
_sourceCategory=herokuParse Expression. For each Heroku application reporting data to Sumo, enter a statement that renames the
_sourceNamefrom the drain ID to the application name. For example:if (_sourceName="Drain_ID", "Application_Name", _sourceName) as _sourceNameThe FER below changes the value of
_sourceNamefor two applications. The first line changes_sourceNamefrom “d.98ee476d-d2d8-46bf-afc2-740f6f7e5b2a” to “CustApp”. The second line changes_sourceNamefrom “d.00870f28-53f9-4680-b2ab-2287ec9d8637” to “VendorApp”:if (_sourceName="d.98ee476d-d2d8-46bf-afc2-740f6f7e5b2a", "CustApp", _sourceName) as _sourceName| if (_sourceName="d.00870f28-53f9-4680-b2ab-2287ec9d8637", "VendorApp", _sourceName) as _sourceNameClick Add to save the rule.
Searching Heroku application logs
Once Sumo begins ingesting your Heroku application logs, you can use Sumo’s search capabilities to query the data. This section is a brief introduction to searching in Sumo. For comprehensive information, see About Search Basics in Sumo help.
A best practice when running queries in Sumo is to use search metadata, which is metadata that Sumo attaches to log data upon ingestion. Sumo attaches a variety of different metadata fields to your log data—the purpose is to ease the search process. The metadata field you’ll use most commonly in searches is _sourceCategory. The Sumo Logic add-on for Heroku sets the value of _sourceCategory for your Heroku log data to “heroku”. For general information about Sumo metadata, see Search Metadata in Sumo help.
To open a search window in Sumo, click the plus sign (+) at the top of the Sumo app home page, and select Log Search from the drop-down.
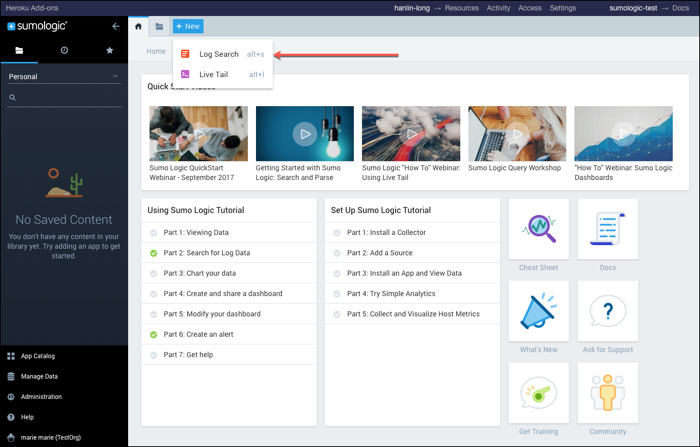
A search tab opens. You enter your query in the search field at the top of the page.
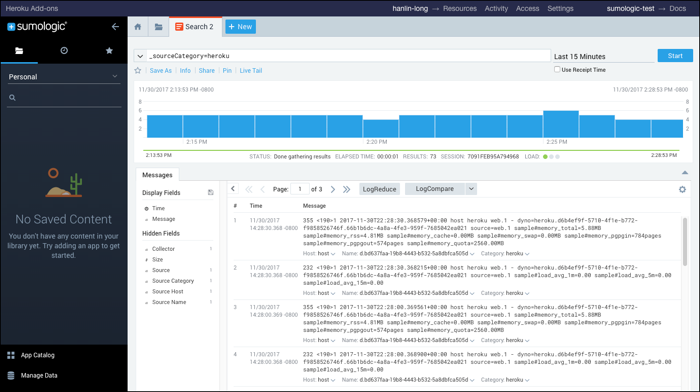
To limit your search to data sent by the Sumo Logic add-on, you start your search with:
_sourceCategory=heroku
The query is valid, and broad—it returns all log messages that are tagged with _sourceCategory of “heroku”. The results are shown in the lower part of the page, as shown below.
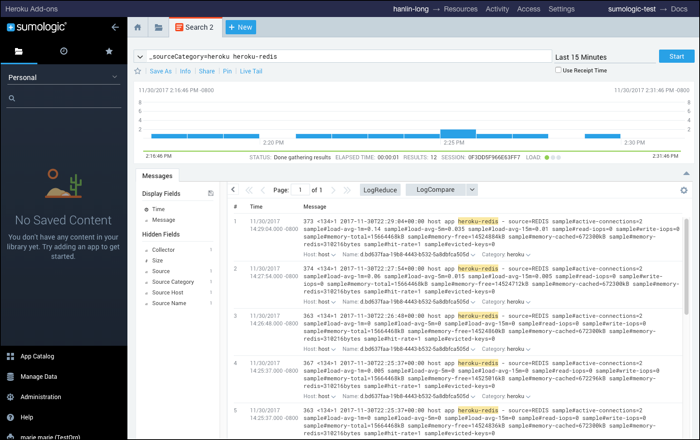
To narrow down the search you can add a keyword. For example, run this query to return log messages tagged “heroku” that contain the string “heroku-redis”:
_sourceCategory=heroku heroku-redis
Note that in the results, the keyword you entered is highlighted.
If you defined a field extraction rule to rename the _sourceName metadata field from the Logplex drain UUID to a meaningful name, you can scope your queries using _sourceName=AppName , where AppName is a name you assigned in the FER.
Removing the add-on
You can remove the Sumo Logic add-on with the Heroku CLI.
This cannot be undone!
$ heroku addons:destroy sumologic
-----> Removing sumologic from sharp-mountain-4005... done, v20 (free)
Support
All Sumo Logic support and runtime issues should be submitted via one of the Heroku Support channels.